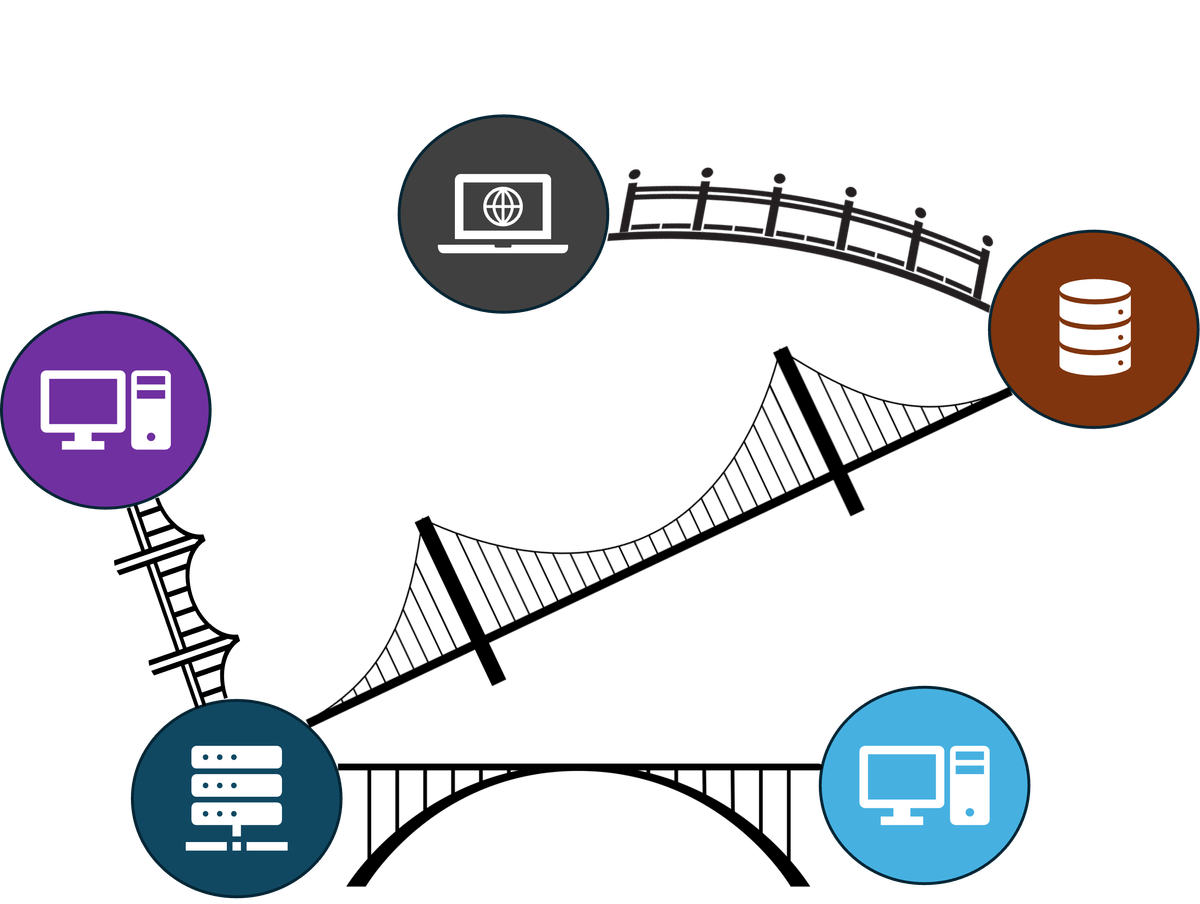
In today’s tech-driven world, component-based architecture and API-driven integrations play a crucial role in enabling scalable and modular digital systems. APIs, the bridges between different systems, services and components, allow for exchange of information and help the seemingly disconnected components to act as a whole.
But this interconnectedness comes with challenges, especially security. Every API endpoint, integration, or component is a potential entry point for attackers. So, how do we keep our systems secure while staying connected?
Excessive Data Exposure and Broken Access Control
Breaking applications into smaller, reusable modules is smart, but it can create security headaches. One major issue is excessive data exposure, APIs often return more data than needed, assuming the client will filter it. Unfortunately, attackers can exploit this oversharing.
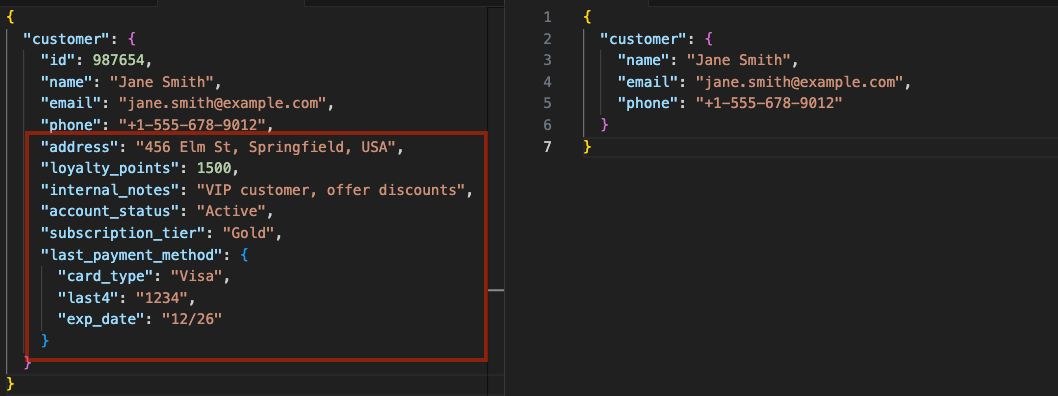
Imagine an API for a customer database that returns internal IDs, passwords, or unnecessary metadata when all the client needs is a name and email. Or a mobile app fetching user profiles but accidentally exposing credit card details. These oversights pose serious risks, especially if attackers intercept or manipulate API calls.
Every year, the Open Web Application Security Project (OWASP) publishes a list of the most critical security risks. Leading the pack? Broken Access Control. Even organizations that appear highly secure can unknowingly expose sensitive data.
The good news? There are ways to protect against this, starting with strict access control. But enforcing security in an API-driven world isn’t simple: should you split existing APIs, adopt a Zero Trust model, deploy an API Security Gateway, or something else entirely?
This is just the beginning! In the full article, we’ll dive into security strategies, trade-offs, and how to protect APIs without sacrificing connectivity. Stay tuned—subscribe to get notified as soon as it drops!