APIs: The Bridges We Build and Need to Defend
In today’s tech-driven world, component-based architecture and API-driven integrations play a crucial role in enabling scalable and modular digital systems. APIs, the bridges between different systems, services and components, allow for exchange of information and helps the seemingly disconnected components to act as a whole.
But this interconnectedness comes with challenges, especially security. Every API endpoint, integration, or component is a potential entry point for attackers. So, how do we keep our systems secure while staying connected?
Excessive data exposure and broken access control
Breaking applications into smaller, reusable modules is smart, but it can create headaches for security. One big issue is excessive data exposure in APIs. Developers often design APIs with multiple use cases in mind, assuming the client will filter out unnecessary data. Unfortunately, attackers can exploit this “oversharing” to their advantage.
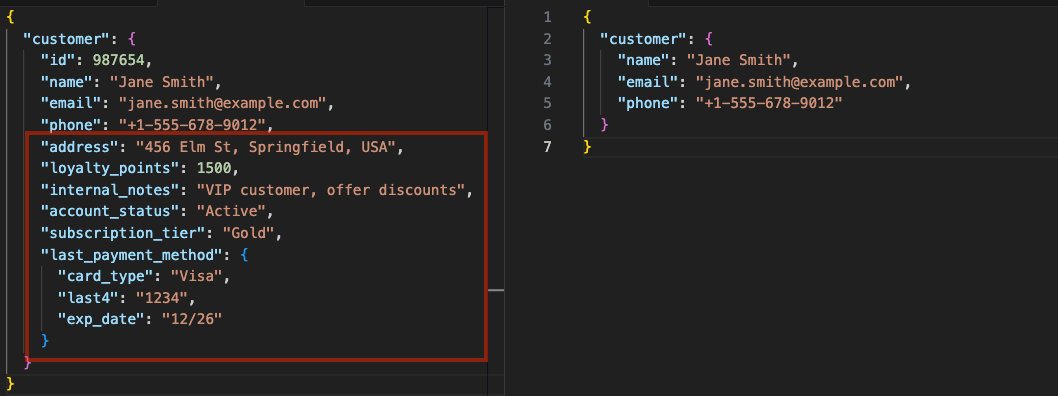
Imagine an API for a customer database that returns a payload with sensitive information like internal IDs, passwords, or unnecessary metadata when all the client needs is a name and email. Or consider a mobile app fetching user profile data and accidentally exposing credit card details in its API response. Even small details such as internal notes which could leak business logic can present a security risk. This over-sharing creates major risks, especially if attackers intercept or manipulate these calls to grab sensitive information.
Every year, the Open Web Application Security Project (OWASP) publishes the OWASP top 10, a list of the most critical security risks to applications. This list serves as a reference for developers, security professionals, and organizations to identify and mitigate vulnerabilities, ensuring robust application security practices. And leading the pack in the latest edition? Broken Access Control. This risk often stems from unauthorized exposure of sensitive data, a problem even the most secure-looking organizations might not realize they have.
In our example, part of the problem starts when APIs are designed as large, monolithic endpoints that expose excessive data. Instead of a single API call returning all customer information, potentially including sensitive details, breaking it into separate endpoints improves security and access control. A more secure approach is to have distinct APIs like: one for public information, another for financial data, and a final one for sensitive personal details. This API segmentation allows for fine-grained access control, ensuring that only authorized users and systems retrieve specific types of data, reducing the risk of unintended exposure or breaches.
The good news? There are ways to protect against these risks, starting with strict access control over exposed information. API segmentation is one step, but true security requires enforcing who can access what and when. And what is more strict than not trusting anything at all?
Zero Trust Security Model
Think of traditional IT network security like a medieval castle: surrounded by a moat, tough to break into, but easy to roam freely once you’re inside. For trusted individuals, this setup is great! You can move around unbothered. But what happens when attackers sneak in? They gain free rein over everything. Not exactly ideal.
Enter the Zero Trust security model, which flips the castle metaphor on its head. Instead of trusting someone just because they’re "inside", Zero Trust treats everyone as a potential threat. Think of it as having guards who verify your identity every time you open a door or take a book off a shelf. Zero Trust security's core ideas is simple: "Never trust, always verify".
In summary, Zero Trust emphasizes that no entity, whether inside or outside the network, should be inherently trusted. Instead, all access must be continuously validated and monitored.
But now, how should those guards be implemented in real systems? Let us go back to how these access control guards are implemented other types of systems.
The basics of Access Control
Humans have been controlling access for ages, think locked doors, gates, and passwords. The same principle applies to today’s digital resources.
There are multiple ways to control access to resources, but the idea is simple: we want to relate subject identities to resources. The most simple approach for this is to just create a list of subject-resource pairs. This is known as an Access Control List (ACL), and it was used in computer systems from the moment multi-user systems were introduced. While this works for small setups, it can become a mess in complex, multi-user systems.
Modern solutions like Attribute-Based Access Control (ABAC) and Policy-Based Access Control (PBAC) simplify access management in complex systems. Instead of mapping individual users to specific resources, these models rely on attributes (e.g., role, department, or location) and policies to dynamically determine access. This abstraction shifts the focus from managing individual identities to managing groups and roles, making it far easier to scale access control in large systems.
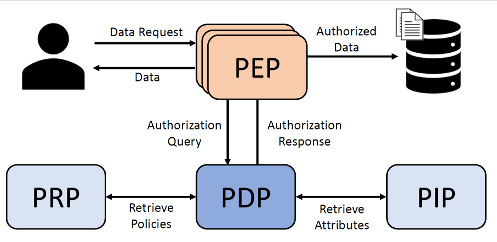
Central to these approaches is the concept of a policy enforcement point (PEP), which acts as a gatekeeper for incoming requests. The PEP evaluates requests against predefined policies and attributes, applying access control dynamically based on context. For example, an ABAC system might allow access to a resource if the user belongs to a specific department and is accessing it during work hours. This approach ensures fine-grained control, reduces administrative overhead, and enforces least-privilege principles effectively.
And here’s the kicker: these principles integrate beautifully into API-driven architectures!
API Security gateway
So, how does this all tie into a component based architecture? Well, enter API Security Gateways.
Unlike traditional API gateways, which focus on monitoring and logging, API Security Gateways act as centralized enforcers of security policies. They intercept API requests, validate them, and ensure they comply with your security rules before reaching backend services.

API security gateways offer several key features, including the ability to intercept and validate each request against security policies, such as token authentication and authorization checks. Schema validation also plays a key role here—ensuring that incoming API requests conform to expected structures prevents injection attacks and malformed requests.
Among other things, being able to process each request makes possible to perform data filtering to the request to enable fine-granular access control. Enforcing least-privilege principles by exposing only the necessary data.
By implementing an API security gateway, you can centralize authentication and authorization processes, making it easier to enforce robust security measures like Zero Trust. These gateways also enable logging and monitoring: tracking API traffic to detect unusual patterns and perform post-incident analysis.
However, as with anything in tech, there’s no free lunch. These gateways introduces an additional layer of complexity, but a necessary one if the security of the data is a serious concern.
Having a centralized approach to the enforcement of authorization in the APIs has several side effects, including performance overhead through additional checks, and the additional architectural complexity bringing extra planning and maintenance. And not even get me started with an added single point of failure in our system!
Some final thoughts
Securing APIs in a component-based architecture requires a strategic approach. By understanding risks like excessive data exposure and broken access control, adopting models like Zero Trust, and leveraging tools like API security gateways, you can safeguard your systems against modern threats.
Remember to keep learning, stay updated on best practices, and embrace a proactive security mindset, it’s an investment in protecting what matters most. By exploring successful implementations of these systems and staying informed about best practices, you can unlock their full potential while minimizing risks. Stay tuned for more insights and strategies on mastering API security.


